WannaCry is a ransomware program first detected on Friday, May 12, targeting vulnerabilities in Microsoft software. Since the onset of the attack, it is estimated that 200,000 computers in 150 countries have been affected.
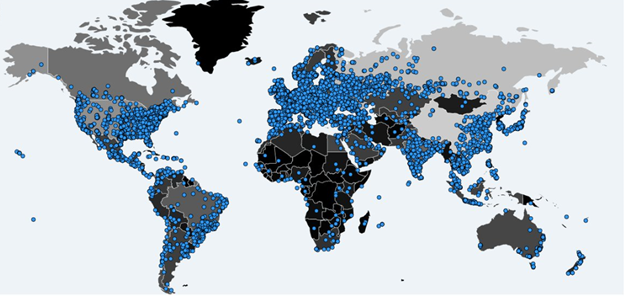
Source: http://cyberwar.liveuamap.com/en/2017/14-may-past-24-hours-wannacry-infection-map
WannaCry utilizes the “EternalBlue” SMBv2 exploit, believed to be developed by the NSA and leaked to the public by the “Shadow Brokers” hacker group on April 14th, 2017. While a patch was released by Microsoft on March 14th, 2017 (MS Bulletin MS17-010), unpatched devices and legacy systems (systems like Windows XP that no longer receive security patches) are still vulnerable.
The initial infection appears to have resulted from a malicious phishing email, however once a device is compromised, the malware spreads through the networks as a worm, scanning and exploiting connected devices.
Upon successfully infecting a system, the WannaCry malware installs an encryption package that targets commonly used files, such as audio, video and text documents:
The following image shows a comprehensive list of targeted file extensions:

Infected systems will then display a pop-up window, informing the users that their files have been encrypted and providing instructions and links for payment and decryption.
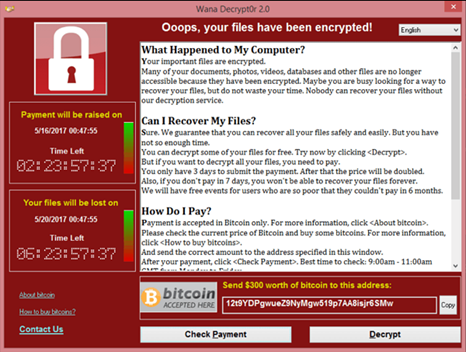
Next Steps and Protection
While the spread of the WannaCry worm was greatly slowed by a “kill-switch” being triggered this weekend, it is extremely likely that new, more resilient versions will be released.
In order to ensure users and networks are protected from various versions of this and other malware, the following practices should be employed:
- Phishing attempts contained a zip file. If it is acceptable to normal business operation, zip attachments should be blocked at the email filter.
- Ensure network ports TCP 445 and 139 are not open to inbound internet traffic on corporate firewalls
- Decommission or replace legacy/non-supported software or systems
- Apply Microsoft security patches and updates
- Ensure anti-virus protection is up to date and conducting regularly-scheduled or real-time scans
- Educate employees and users about safe online practices, such as not navigating to untrusted websites and validating URL links.
- Educate employees and users about safe email practices, such as how to identify phishing attempts and not opening emails, attachments or links from unknown sources.
- Disable non-required services (ie: RDP, VNC, etc.)
- Ensure all critical data is backed-up on a regular schedule



